






We have integrated the French STid product family, a pioneer in encrypted card readers, into the Predor system. STid's proprietary SSCP protocol and AES128 encryption protects data over the entire data line from end-to-end (SSCP add-on panel must be connected). The Predor system uses the most up-to-date encryption algorithms on all channels.
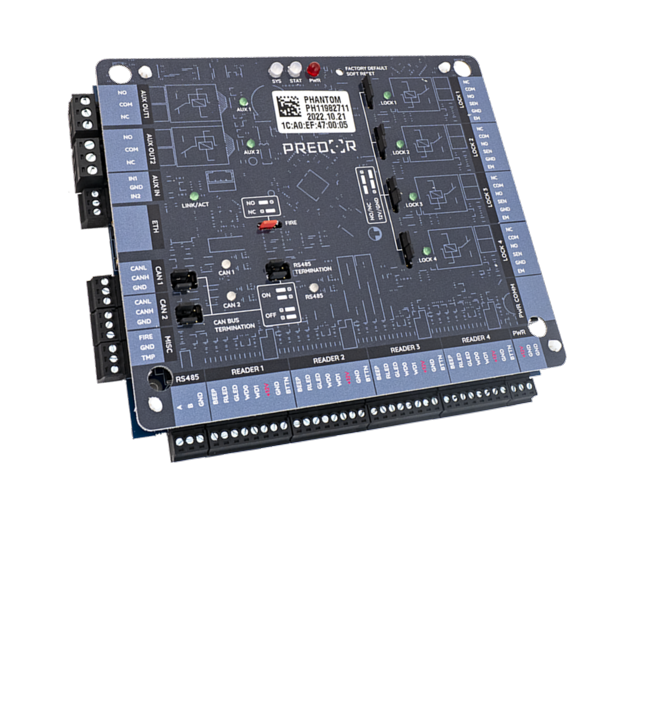
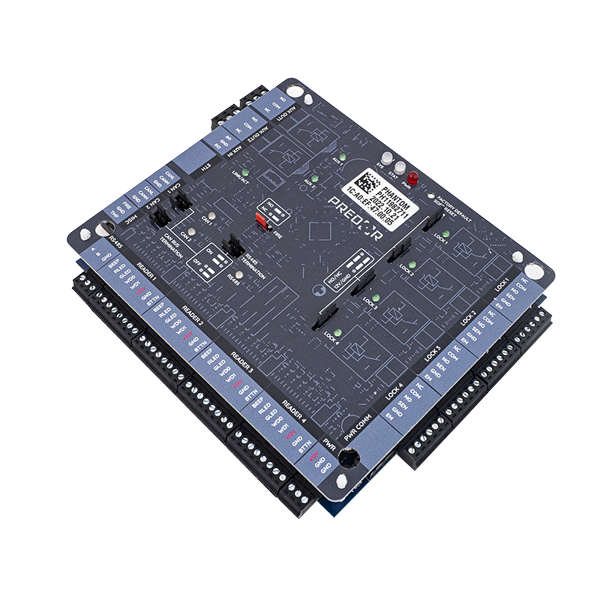
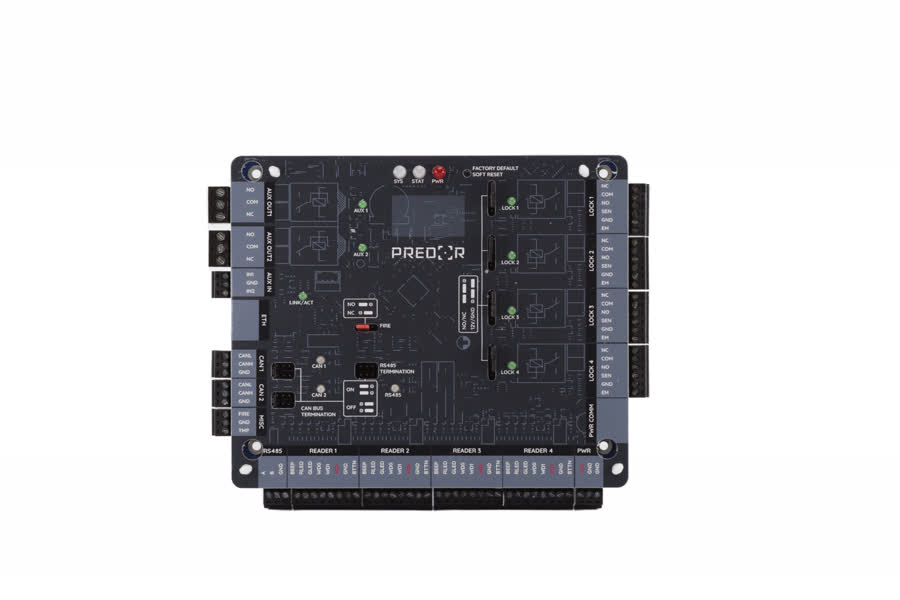
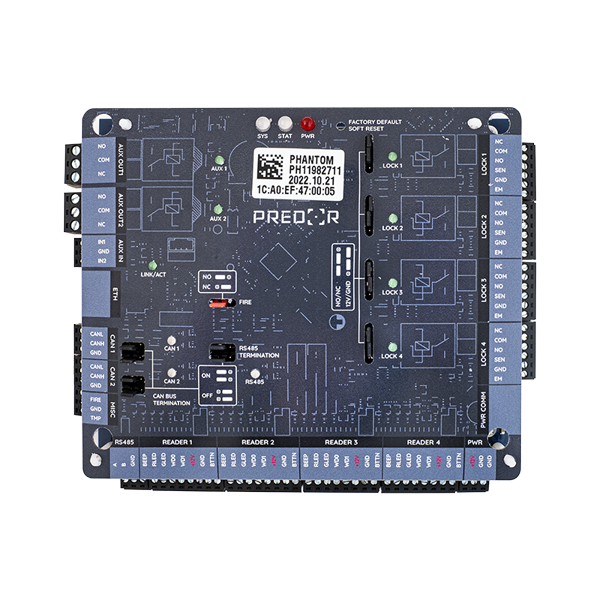
The Predor Phantom controller has a much more powerful processor and more memory than its predecessor. It can be easily integrated with modern security systems thanks to its many new peripherals. We can implement integration with any system to meet specific requirements.
The system creates a wiring diagram for each controller according to the current settings, which can even be printed out.
The controller can store up to 100 000 users, 200 000 IDs and 250 000 events, so it can perform access control tasks perfectly in standalone mode, without any server connection.
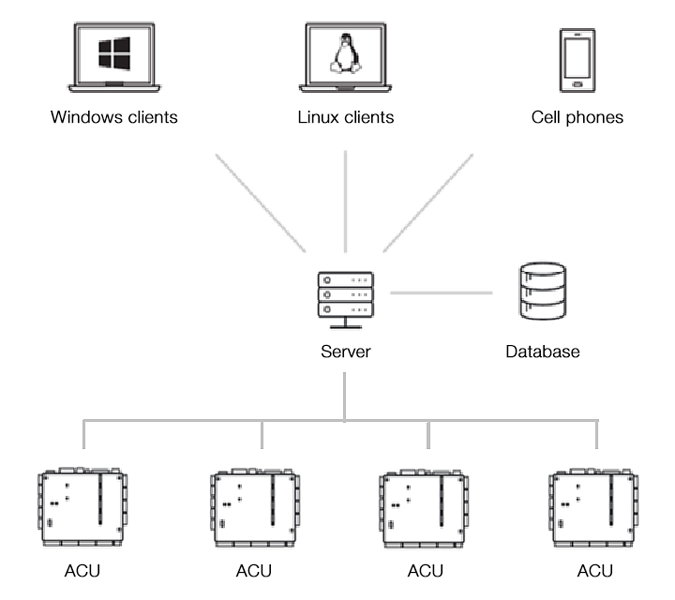
Automatic network discovery allows the client to automatically find all networked controllers. The complete setup of the system to be installed can be done at home, all you need to do is upload the settings on site.
2-2 inputs and relay outputs can be used for integration with other systems, devices or for multi-stage control. Examples include probing or package inspection.


Contact our team for a personalised quote for your business
Contact us for a personalised quote or online software demonstration
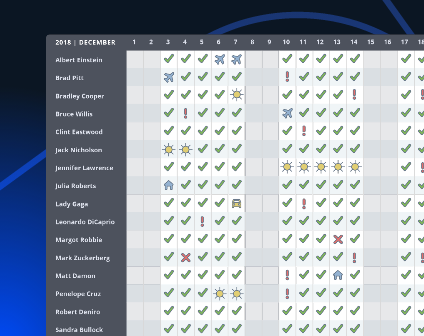
It reduces administrative burdens and increase your company's efficiency. Managers can get a quick and easy overview of important worktime information.
Go to datasheet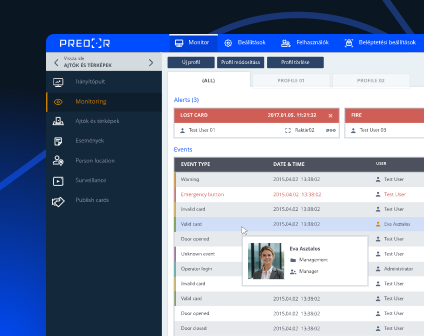
Its flexibility and modular structure makes it ideal for small-, middle- and large scale companies alike, can adapt is for their needs.
Go to datasheet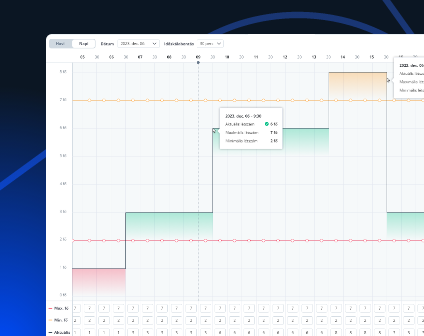
The system automatically detects suboptimal shift plans, and helps to avoid both under- and over-allocation.
Go to datasheet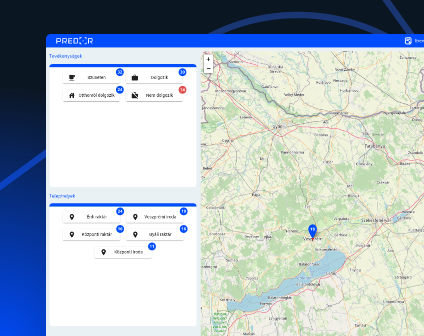
Keep track of your remote working employees. No server maintenance or large upfront cost necessary.
Go to datasheet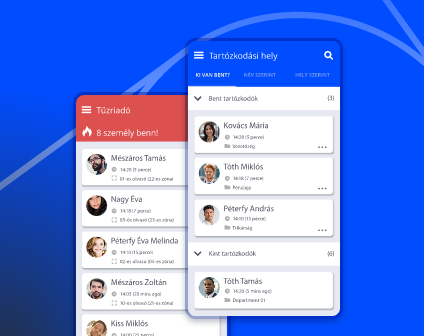
Use our free mobile app to access your security reports and monitor your system real time, anywhere, anytime.
Go to datasheet
Its clean design, built in RGB LED strpe and Wi-Fi compatibility makes this product perfect for offices and community spaces.
Go to datasheet
The device can easily be mounted on a wall bracket, and offices can take advantage of its wireless capabilites.
Go to datasheet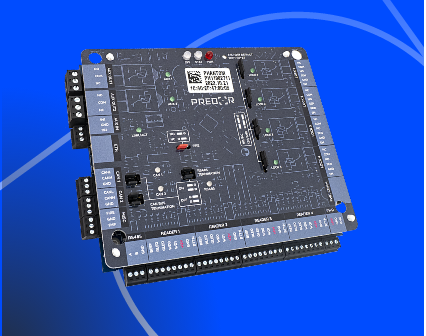
This extremly reliable product can serve high security locations, and it can control any mechanical access control device.
Go to datasheet
The card reader family integrated with Predor represents the cutting edge of high security. It protects the card data with the most sophisticated encyption, end-to-end.
Go to datasheet
Complete entry point assembled and delivered in a container. We offer ubeatable prices for excellent 10 and 20 legged container. Predor is compatible with the hungarian Üvegkapu system.
Go to datasheet